Your personal information might be available on the dark web without you even knowing it. When companies experience data breaches, the exposed data often ends up in this part of the internet where it can be sold or traded. This includes email addresses, phone numbers, passwords, and even home addresses.
Google now offers a way to check if any of your data has appeared in these breaches through its dark web report, a feature built into Google One. It scans known sources on the dark web and alerts you to any matches.
Make Sure You Have Google One
Step 1: Go to https://one.google.com.
Step 2: Click ‘Learn more.’

Step 3: Choose a plan.

Step 4: Complete payment and sign in.
Open the Dark Web Report Page
Step 1: Go to https://myactivity.google.com/dark-web-report/setup-profile?pli=1.
Step 2: Sign in with your Google account.

It will take you to the dark web monitoring dashboard.
Review the Information That Was Scanned
Step 1: Click ‘Select all’ then ‘Allow.’

Step 2: Select other data to include, such as phone number, name, other email addresses, or your mailing address.

Step 3: Confirm and start the scan.
Click ‘Done’ after you select your information. Google will begin checking sources on the dark web. Once you complete this, it should take you to the report dashboard.
Note: The scan usually takes less than a minute. Stay on the page while it’s completed.

Step 4: View your report.
Once the scan finishes, click ‘View all results.’ If the system finds any of your personal data, you’ll see a list of data breach entries. Each entry should include:
- The site or service affected
- The date of the breach
- The type of data the breach leaked


Step 5: Expand entries for more detail.
You can click each entry to see which of your email addresses, passwords, or accounts the dark web has exposed.

Step 6: Take action if your data was exposed.
Google will sometimes offer recommended actions to protect your data. These usually include:
- Changing passwords immediately
- Enabling two-factor authentication (2FA)
- Keeping an eye on financial accounts
- Freezing your cards

Edit Monitoring Profile
Step 1: Scroll to ‘Edit monitoring profile.’
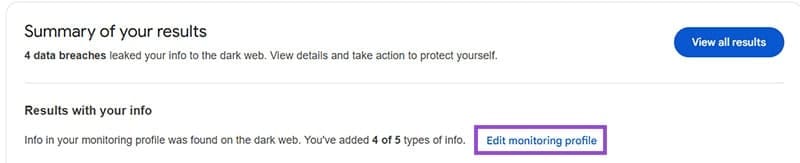
Step 2: Edit any information that is incorrect.
Remember to change the information on the dark web dashboard when you update addresses, emails or passwords.
How Data Breaches Happen
Data breaches typically occur when hackers exploit security flaws in websites, apps, or networks. These attacks can involve phishing, malware, or direct hacking of poorly protected databases. Once inside, attackers steal sensitive information, often selling it on the dark web or using it for identity theft. Even large, well-known companies can fall victim.
Was this helpful?
Last updated on 30 May, 2025
The article above may contain affiliate links which help support Guiding Tech. The content remains unbiased and authentic and will never affect our editorial integrity.